| 基线检查工具 | 您所在的位置:网站首页 › docker安全基线 › 基线检查工具 |
基线检查工具
|
docker官方提供安全扫描工具用于检查有关在生产中部署Docker容器的安全问题。
这种类似于安全扫描类似于安全基线检查,对相应的项进行逐条核查,可以有效地规避一些安全风险。
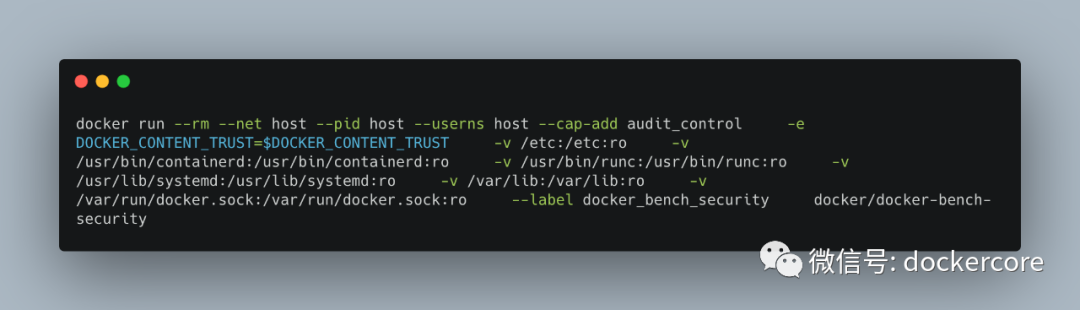
他的github地址:https://github.com/docker/docker-bench-security 使用方法如下: docker run --rm --net host --pid host --userns host --cap-add audit_control -e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST -v /etc:/etc:ro -v /usr/bin/containerd:/usr/bin/containerd:ro -v /usr/bin/runc:/usr/bin/runc:ro -v /usr/lib/systemd:/usr/lib/systemd:ro -v /var/lib:/var/lib:ro -v /var/run/docker.sock:/var/run/docker.sock:ro --label docker_bench_security docker/docker-bench-security如图所示:
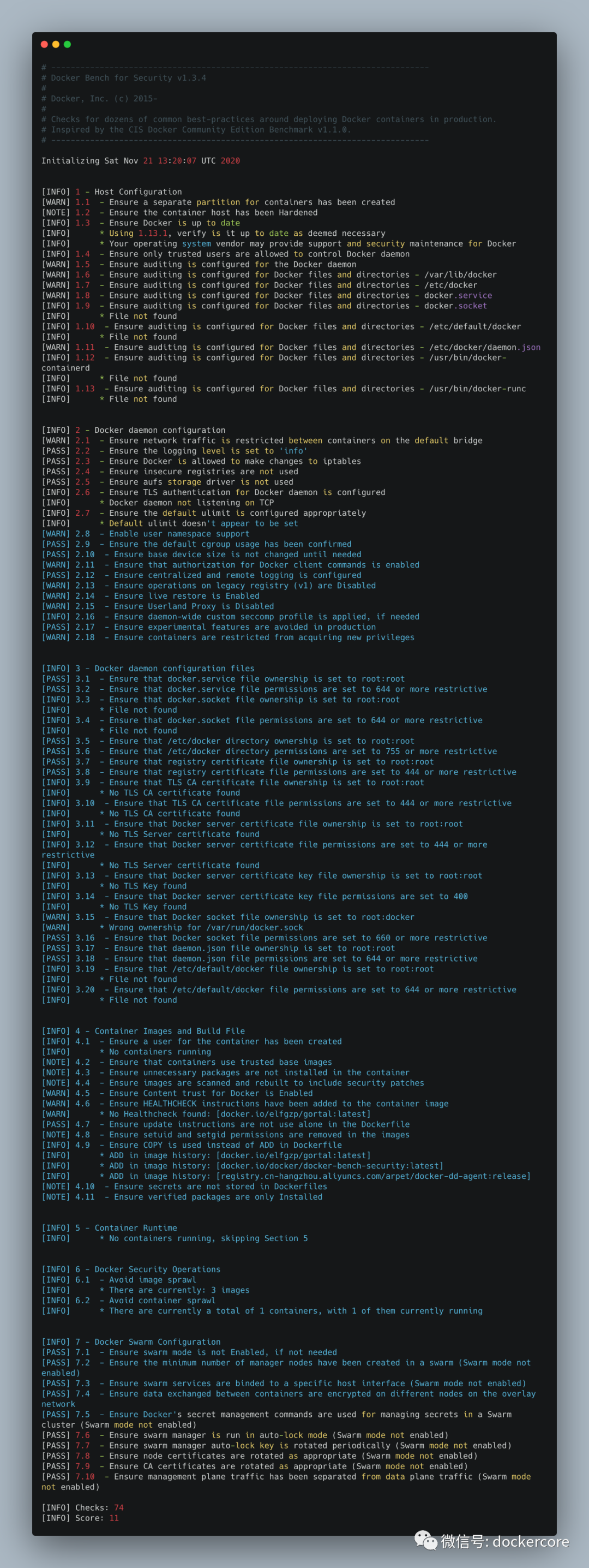
执行完成之后可以看到下面的结果 [[email protected] ~]# docker run --rm --net host --pid host --userns host --cap-add audit_control -e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST -v /etc:/etc:ro -v /usr/bin/containerd:/usr/bin/containerd:ro -v /usr/bin/runc:/usr/bin/runc:ro -v /usr/lib/systemd:/usr/lib/systemd:ro -v /var/lib:/var/lib:ro -v /var/run/docker.sock:/var/run/docker.sock:ro --label docker_bench_security docker/docker-bench-security# ------------------------------------------------------------------------------# Docker Bench for Security v1.3.4## Docker, Inc. (c) 2015-## Checks for dozens of common best-practices around deploying Docker containers in production.# Inspired by the CIS Docker Community Edition Benchmark v1.1.0.# ------------------------------------------------------------------------------Initializing Sat Nov 21 13:20:07 UTC 2020[INFO] 1 - Host Configuration[WARN] 1.1 - Ensure a separate partition for containers has been created[NOTE] 1.2 - Ensure the container host has been Hardened[INFO] 1.3 - Ensure Docker is up to date[INFO] * Using 1.13.1, verify is it up to date as deemed necessary[INFO] * Your operating system vendor may provide support and security maintenance for Docker[INFO] 1.4 - Ensure only trusted users are allowed to control Docker daemon[WARN] 1.5 - Ensure auditing is configured for the Docker daemon[WARN] 1.6 - Ensure auditing is configured for Docker files and directories - /var/lib/docker[WARN] 1.7 - Ensure auditing is configured for Docker files and directories - /etc/docker[WARN] 1.8 - Ensure auditing is configured for Docker files and directories - docker.service[INFO] 1.9 - Ensure auditing is configured for Docker files and directories - docker.socket[INFO] * File not found[INFO] 1.10 - Ensure auditing is configured for Docker files and directories - /etc/default/docker[INFO] * File not found[WARN] 1.11 - Ensure auditing is configured for Docker files and directories - /etc/docker/daemon.json[INFO] 1.12 - Ensure auditing is configured for Docker files and directories - /usr/bin/docker-containerd[INFO] * File not found[INFO] 1.13 - Ensure auditing is configured for Docker files and directories - /usr/bin/docker-runc[INFO] * File not found[INFO] 2 - Docker daemon configuration[WARN] 2.1 - Ensure network traffic is restricted between containers on the default bridge[PASS] 2.2 - Ensure the logging level is set to 'info'[PASS] 2.3 - Ensure Docker is allowed to make changes to iptables[PASS] 2.4 - Ensure insecure registries are not used[PASS] 2.5 - Ensure aufs storage driver is not used[INFO] 2.6 - Ensure TLS authentication for Docker daemon is configured[INFO] * Docker daemon not listening on TCP[INFO] 2.7 - Ensure the default ulimit is configured appropriately[INFO] * Default ulimit doesn't appear to be set[WARN] 2.8 - Enable user namespace support[PASS] 2.9 - Ensure the default cgroup usage has been confirmed[PASS] 2.10 - Ensure base device size is not changed until needed[WARN] 2.11 - Ensure that authorization for Docker client commands is enabled[PASS] 2.12 - Ensure centralized and remote logging is configured[WARN] 2.13 - Ensure operations on legacy registry (v1) are Disabled[WARN] 2.14 - Ensure live restore is Enabled[WARN] 2.15 - Ensure Userland Proxy is Disabled[INFO] 2.16 - Ensure daemon-wide custom seccomp profile is applied, if needed[PASS] 2.17 - Ensure experimental features are avoided in production[WARN] 2.18 - Ensure containers are restricted from acquiring new privileges[INFO] 3 - Docker daemon configuration files[PASS] 3.1 - Ensure that docker.service file ownership is set to root:root[PASS] 3.2 - Ensure that docker.service file permissions are set to 644 or more restrictive[INFO] 3.3 - Ensure that docker.socket file ownership is set to root:root[INFO] * File not found[INFO] 3.4 - Ensure that docker.socket file permissions are set to 644 or more restrictive[INFO] * File not found[PASS] 3.5 - Ensure that /etc/docker directory ownership is set to root:root[PASS] 3.6 - Ensure that /etc/docker directory permissions are set to 755 or more restrictive[PASS] 3.7 - Ensure that registry certificate file ownership is set to root:root[PASS] 3.8 - Ensure that registry certificate file permissions are set to 444 or more restrictive[INFO] 3.9 - Ensure that TLS CA certificate file ownership is set to root:root[INFO] * No TLS CA certificate found[INFO] 3.10 - Ensure that TLS CA certificate file permissions are set to 444 or more restrictive[INFO] * No TLS CA certificate found[INFO] 3.11 - Ensure that Docker server certificate file ownership is set to root:root[INFO] * No TLS Server certificate found[INFO] 3.12 - Ensure that Docker server certificate file permissions are set to 444 or more restrictive[INFO] * No TLS Server certificate found[INFO] 3.13 - Ensure that Docker server certificate key file ownership is set to root:root[INFO] * No TLS Key found[INFO] 3.14 - Ensure that Docker server certificate key file permissions are set to 400[INFO] * No TLS Key found[WARN] 3.15 - Ensure that Docker socket file ownership is set to root:docker[WARN] * Wrong ownership for /var/run/docker.sock[PASS] 3.16 - Ensure that Docker socket file permissions are set to 660 or more restrictive[PASS] 3.17 - Ensure that daemon.json file ownership is set to root:root[PASS] 3.18 - Ensure that daemon.json file permissions are set to 644 or more restrictive[INFO] 3.19 - Ensure that /etc/default/docker file ownership is set to root:root[INFO] * File not found[INFO] 3.20 - Ensure that /etc/default/docker file permissions are set to 644 or more restrictive[INFO] * File not found[INFO] 4 - Container Images and Build File[INFO] 4.1 - Ensure a user for the container has been created[INFO] * No containers running[NOTE] 4.2 - Ensure that containers use trusted base images[NOTE] 4.3 - Ensure unnecessary packages are not installed in the container[NOTE] 4.4 - Ensure images are scanned and rebuilt to include security patches[WARN] 4.5 - Ensure Content trust for Docker is Enabled[WARN] 4.6 - Ensure HEALTHCHECK instructions have been added to the container image[WARN] * No Healthcheck found: [docker.io/elfgzp/gortal:latest][PASS] 4.7 - Ensure update instructions are not use alone in the Dockerfile[NOTE] 4.8 - Ensure setuid and setgid permissions are removed in the images[INFO] 4.9 - Ensure COPY is used instead of ADD in Dockerfile[INFO] * ADD in image history: [docker.io/elfgzp/gortal:latest][INFO] * ADD in image history: [docker.io/docker/docker-bench-security:latest][INFO] * ADD in image history: [registry.cn-hangzhou.aliyuncs.com/arpet/docker-dd-agent:release][NOTE] 4.10 - Ensure secrets are not stored in Dockerfiles[NOTE] 4.11 - Ensure verified packages are only Installed[INFO] 5 - Container Runtime[INFO] * No containers running, skipping Section 5[INFO] 6 - Docker Security Operations[INFO] 6.1 - Avoid image sprawl[INFO] * There are currently: 3 images[INFO] 6.2 - Avoid container sprawl[INFO] * There are currently a total of 1 containers, with 1 of them currently running[INFO] 7 - Docker Swarm Configuration[PASS] 7.1 - Ensure swarm mode is not Enabled, if not needed[PASS] 7.2 - Ensure the minimum number of manager nodes have been created in a swarm (Swarm mode not enabled)[PASS] 7.3 - Ensure swarm services are binded to a specific host interface (Swarm mode not enabled)[PASS] 7.4 - Ensure data exchanged between containers are encrypted on different nodes on the overlay network[PASS] 7.5 - Ensure Docker's secret management commands are used for managing secrets in a Swarm cluster (Swarm mode not enabled)[PASS] 7.6 - Ensure swarm manager is run in auto-lock mode (Swarm mode not enabled)[PASS] 7.7 - Ensure swarm manager auto-lock key is rotated periodically (Swarm mode not enabled)[PASS] 7.8 - Ensure node certificates are rotated as appropriate (Swarm mode not enabled)[PASS] 7.9 - Ensure CA certificates are rotated as appropriate (Swarm mode not enabled)[PASS] 7.10 - Ensure management plane traffic has been separated from data plane traffic (Swarm mode not enabled)
从上图结果可以看到其中标红【WARN】是需要改进的,标绿【PASS】表示通过检测,【INFO】项的话,看需要是否进行调整,如调整完成,可在重新检测规避风险。 关注我让你成为云端最靓的builder
|
【本文地址】
公司简介
联系我们