| scapy学习笔记(1) | 您所在的位置:网站首页 › win10虚拟网卡安装哪一个版本好 › scapy学习笔记(1) |
scapy学习笔记(1)
|
文章目录
1 scapy简介2 安装和运行scapy3 查看当前网络配置3.1 conf概览3.2 查看网卡及路由3.2.1 查看网卡3.2.2 查看路由3.3.3 查看默认网卡
1 scapy简介
scapy是一个python语言写的,用来操作TCP/IP数据包的库,基本涵盖了wireshark的主要功能,例如抓包、ping、traceroute、嗅探、扫描,但由于其可以按照自己的意愿来拼接和“无中生成”TCP/IP数据包中的内容,因此还可以实现attack的部分功能,并可以移植到任意平台运行。 2 安装和运行scapyscapy官网上有安装教程,不再赘述。建议在venv的虚拟环境下安装Scapy的basic包,不影响主python环境。本文是在windows10+python3.7环境下,安装的scapy2.4.3 basic包。另在windows下使用scapy需要安装npcap软件。 运行venv\Scripts下运行activate进入虚拟环境,再运行scapy。 图中INFO错误是scapy的附加功能,需要依赖一些三方包,不安装也不影响scapy核心功能的使用。 默认主题效果: venv/Lib/site-packages/scapy/config.py下有一个Conf类,主要存储了scapy最主要的一些配置,比如scapy版本、主题颜色、网卡、路由、是否使用npcap、可以在scapy交互环境中使用哪些命令等。在scapy交互环境中可以直接输入conf来查看相应的内容。 3.1 conf概览 命令作用conf显示conf所有配置conf.iface主网卡conf.route获取主路由conf.commands可在交互环境中使用的命令集合lsc()同conf.commands详解: conf本质是Conf类的实例: >>> type(conf) scapy.config.ConfConf类中包含有大量配置,部分配置如下: >>> conf ASN1_default_codec = AS_resolver = conf.iface当前路由表conf.route(部分) >>> conf.route Network Netmask Gateway Iface Output IP Metric 0.0.0.0 0.0.0.0 25.255.255.254 ZeroTier One Virtual Port 172.28.33.102 10034 0.0.0.0 0.0.0.0 10.11.91.254 Intel(R) Ethernet Connection (5) I219-V #2 10.11.91.161 25 10.11.91.0 255.255.255.0 0.0.0.0 Intel(R) Ethernet Connection (5) I219-V #2 10.11.91.161 281 10.11.91.161 255.255.255.255 0.0.0.0 Intel(R) Ethernet Connection (5) I219-V #2 10.11.91.161 281 10.11.91.255 255.255.255.255 0.0.0.0 Intel(R) Ethernet Connection (5) I219-V #2 10.11.91.161 281 127.0.0.0 255.0.0.0 0.0.0.0 Npcap Loopback Adapter 127.0.0.1 281 127.0.0.1 255.255.255.255 0.0.0.0 Npcap Loopback Adapter 127.0.0.1 281可在交互环境中使用的命令conf.commands(或者输入lsc() ) >>> conf.commands IPID_count : Identify IP id values classes in a list of packets arpcachepoison : Poison target's cache with (your MAC,victim's IP) couple arping : Send ARP who-has requests to determine which hosts are up arpleak : Exploit ARP leak flaws, like NetBSD-SA2017-002. bind_layers : Bind 2 layers on some specific fields' values. bridge_and_sniff : Forward traffic between interfaces if1 and if2, sniff and return chexdump : Build a per byte hexadecimal representation computeNIGroupAddr : Compute the NI group Address. Can take a FQDN as input parameter corrupt_bits : Flip a given percentage or number of bits from a string corrupt_bytes : Corrupt a given percentage or number of bytes from a string defrag : defrag(plist) -> ([not fragmented], [defragmented], defragment : defragment(plist) -> plist defragmented as much as possible dhcp_request : Send a DHCP discover request and return the answer dyndns_add : Send a DNS add message to a nameserver for "name" to have a new "rdata" dyndns_del : Send a DNS delete message to a nameserver for "name" etherleak : Exploit Etherleak flaw explore : Function used to discover the Scapy layers and protocols. fletcher16_checkbytes: Calculates the Fletcher-16 checkbytes returned as 2 byte binary-string. fletcher16_checksum : Calculates Fletcher-16 checksum of the given buffer. fragleak : -- fragleak2 : -- fragment : Fragment a big IP datagram fuzz : getmacbyip : Return MAC address corresponding to a given IP address getmacbyip6 : Returns the MAC address corresponding to an IPv6 address hexdiff : Show differences between 2 binary strings hexdump : Build a tcpdump like hexadecimal view hexedit : Run hexedit on a list of packets, then return the edited packets. hexstr : Build a fancy tcpdump like hex from bytes. import_hexcap : Imports a tcpdump like hexadecimal view is_promisc : Try to guess if target is in Promisc mode. The target is provided by its ip. linehexdump : Build an equivalent view of hexdump() on a single line ls : List available layers, or infos on a given layer class or name. neighsol : Sends and receive an ICMPv6 Neighbor Solicitation message overlap_frag : Build overlapping fragments to bypass NIPS promiscping : Send ARP who-has requests to determine which hosts are in promiscuous mode rdpcap : Read a pcap or pcapng file and return a packet list report_ports : portscan a target and output a LaTeX table restart : Restarts scapy send : Send packets at layer 3 sendp : Send packets at layer 2 sendpfast : Send packets at layer 2 using tcpreplay for performance sniff : split_layers : Split 2 layers previously bound. sr : Send and receive packets at layer 3 sr1 : Send packets at layer 3 and return only the first answer sr1flood : Flood and receive packets at layer 3 and return only the first answer srbt : send and receive using a bluetooth socket srbt1 : send and receive 1 packet using a bluetooth socket srflood : Flood and receive packets at layer 3 srloop : Send a packet at layer 3 in loop and print the answer each time srp : Send and receive packets at layer 2 srp1 : Send and receive packets at layer 2 and return only the first answer srp1flood : Flood and receive packets at layer 2 and return only the first answer srpflood : Flood and receive packets at layer 2 srploop : Send a packet at layer 2 in loop and print the answer each time tcpdump : Run tcpdump or tshark on a list of packets. tdecode : traceroute : Instant TCP traceroute traceroute6 : Instant TCP traceroute using IPv6 traceroute_map : Util function to call traceroute on multiple targets, then tshark : Sniff packets and print them calling pkt.summary(). wireshark : wrpcap : Write a list of packets to a pcap file 3.2 查看网卡及路由 3.2.1 查看网卡 命令作用get_windows_if_list()获取所有网卡IFACES / ifacesget_windows_if_list() 的全局变量IFACES.reload() / ifaces.reload()网卡发生变化时,刷新IFACES详解: venv/Lib/site-packages/scapy/arch/windows/__init__.py文件get_windows_if_list()用来获取网卡列表: >>> get_windows_if_list() [{'name': '有线网', 'win_index': 27, 'description': 'Intel(R) Ethernet Connection (5) I219-V #2', 'guid': '{XX}', 'mac': 'xx:xx:xx:xx:xx:xx', 'ipv4_metric': 25, 'ipv6_metric': 25, 'ips': ['fe80::XXXX:XXXX:XXXX:XXXX', '10.11.91.161']}, {'name': 'Npcap Loopback Adapter', 'win_index': 22, 'description': 'Npcap Loopback Adapter', 'guid': '{XX}', 'mac': 'xx:xx:xx:xx:xx:xx', 'ipv4_metric': 25, 'ipv6_metric': 25, 'ips': ['fe80::XXXX:XXXX:XXXX:XXXX', '169.254.140.26']}, {'name': 'Wifi', 'win_index': 31, 'description': 'Intel(R) Dual Band Wireless-AC 8265 #2', 'guid': '{XX}', 'mac': 'xx:xx:xx:xx:xx:xx', 'ipv4_metric': 25, 'ipv6_metric': 25, 'ips': ['fe80::XXXX:XXXX:XXXX:XXXX', '169.254.62.191']}]NetworkInterfaceDict中,用NetworkInterface将get_windows_if_list()进行了封装,并在windows/__init__.py中进行了如下初始化,因此可使用IFACES或者ifaces查看网卡列表: IFACES = ifaces = NetworkInterfaceDict() #NetworkInterfaceDict的无参构造函数不包含任何有用信息 IFACES.load() #这里是真正加载本地网卡的,因此如果网卡列表发生了变化,需要手工重新调用下ifaces.reload() >>> ifaces INDEX IFACE IP MAC 27 Intel(R) Ethernet Connection (5) I219-V #2 10.11.91.161 XXX 22 Npcap Loopback Adapter 127.0.0.1 00:00:00:00:00:00 18 SVN Adapter V1.0 169.254.112.118 XXX 29 Microsoft Wi-Fi Direct Virtual Adapter #3 169.254.173.211 XXX 6 Microsoft Wi-Fi Direct Virtual Adapter #4 169.254.192.230 XXX 21 Bluetooth Device (Personal Area Network) #2 169.254.227.190 XXX 17 TAP-Windows Adapter V9 169.254.26.68 XXX 31 Intel(R) Dual Band Wireless-AC 8265 #2 169.254.62.191 XXX 14 ZeroTier One Virtual Port 172.28.33.102 XXX 10 VMware Virtual Ethernet Adapter for VMnet8 192.168.15.1 XXX 23 VMware Virtual Ethernet Adapter for VMnet1 192.168.220.1 XXX -2 [Unknown] NdisWan Adapter None ff:ff:ff:ff:ff:ff -3 [Unknown] NdisWan Adapter None ff:ff:ff:ff:ff:ff -1 [Unknown] NdisWan Adapter None ff:ff:ff:ff:ff:ff如果在使用过程中网卡列表发生了变化,需要手动调用ifaces.reload() class NetworkInterfaceDict(UserDict): def reload(self): """Reload interface list""" self.restarted_adapter = False self.data.clear() if conf.use_pcap: # Reload from Winpcapy from scapy.arch.pcapdnet import load_winpcapy load_winpcapy() self.load() # reload函数实际上最后也是通过调用load重新加载网卡列表 # Reload conf.iface conf.iface = get_working_if() #reload函数会同时刷新默认网卡,这里目前有点问题,详见3.2.3节 3.2.2 查看路由 命令作用read_routes()查看ipv4路由Route()对read_routes()的封装conf.routeRoute的全局对象conf.route.route(dst=“www.baidu.com”)获取去百度的路由,如果dst=None的话返回默认路由conf.route.resync()如果网络发生了变化,用来刷新conf.routevenv/Lib/site-packages/scapy/arch/windows/__init__.py中,read_routes()用来获取ipv4路由 >>> read_routes() [(0, //dest 以十进制显示 0, //netmask 以十进制显示 '10.11.91.254', //nexthop XXX}>, '172.28.33.102', 10034), (168516352, 4294967040, '0.0.0.0', |
【本文地址】
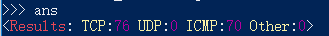
 scapy的默认主题太暗,建议改成亮色,conf.color_theme=BrightTheme()
scapy的默认主题太暗,建议改成亮色,conf.color_theme=BrightTheme()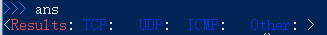 BrightTheme主题效果:
BrightTheme主题效果: